Zilliqa Implements Anti-Fraud Measures with Scam Tracker & $SCAM Token
While maintaining the decentralised nature of the protocol, we aim to protect our global community of token holders by alerting them to potential threats and helping mitigate risks or their losses.
- Zilpay to Automatically Flag Known Phishing Sites — More wallet integrations coming soon!
Introduction
Scams have been prevalent in the cryptosphere (and the internet) since its inception. They come in many forms such as phishing websites or addresses. Within the Ethereum community, an initiative known as CryptoScamDB houses a database of known addresses or domains that are involved in current and past scams. Services such as Metamask and Etherscan use this tool to flag out addresses or websites that are potentially involved in scam-related activities. However, many of such initiatives are chain-specific and may not support other chain asset formats.
As such, we came up with our own version of the scam database for Zilliqa. While maintaining the decentralised nature of the protocol, we aim to protect our global community of token holders by alerting them to potential threats and helping mitigate risks or their losses.
To that effect, this project will:
- Identify and block phishing websites impersonating applications within Zilliqa’s ecosystem
- Flag addresses involved in scams
- Authenticate Zilliqa groups’ Telegram admins
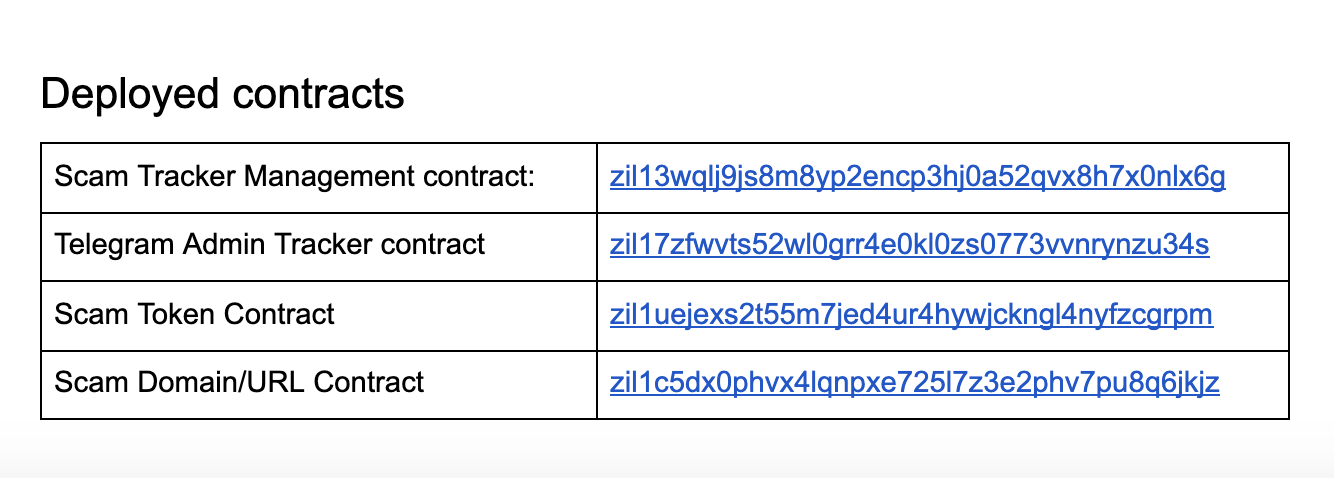
Unlike CryptoscamDB where data is housed within a traditional database, we have gone with the approach of deploying four smart contracts to the related information. These are:
- ScamManagement.scilla — Manage who can add or remove entries in ScamURL.scilla, ScamToken.scilla and ManagerTracking.scilla
- ScamURL.scilla — Store a list of URL or domains involved in scams
- ScamToken.scilla — $SCAM token contract to issue $SCAM to known scam addresses
- ManagerTracking.scilla — Stores a list of Zilliqa Official Telegram chat group admins
Design principles
The team is well aware of censorship concerns from the Zilliqa community. Hence, when designing this system, we adopt a light approach in tackling scams. This means there is no protocol level for blocking in any form. Scam identification is tracked via smart contracts and it is up to ecosystem partners like wallets and explorers to decide whether they would like to integrate and what kind of warning messages they would like to show their users.
In principle, the team is against the hard blocking of any Zilliqa addresses. We would rather have a warning approach and let users decide whether to proceed or not. In the event a wallet decides to go for hard blocking, the wallet owner can choose to import their private key or mnemonics into other wallets and proceed with the transaction at his or her own risk.
Governance
At the start of this project, admins of the Scam Tracker will be restricted to certain Zilliqa team members. We will only enroll addresses or websites that we identified as being part of an ongoing scam. For governance models, we will leave it for future work.
Caveat
This project is not meant for token recovery. If a user has already fallen to the scam and transferred their tokens to the scammer, the tokens cannot be recovered.It is unfortunately out of the scope of this project. Victims of scams are recommended to proceed to contact the support desk of exchanges if the scammed token are transferred to an exchange address.
Scam tracker only tracks known scams by the team members. It will not be able to track all scams.
Code repository and deployed contracts
The contract code and unit test repository can be found at: https://github.com/Zilliqa/ZILScamWatchlist
Identification and blocking phishing website
Whenever a phishing website involving the Zilliqa ecosystem is detected by the team, the Zilliqa team member can proceed to add the scam domain/URL to the “ScamURL.scilla” contract.
Blocking of phishing website can be in two forms:
- Blocking of entire domain
- Blocking of a specific URL eg. google form
Web browser extensions such as ZilPay, can fetch the list of URLs and domains and block such sites or provide a warning when the user visit such sites.

$SCAM Token
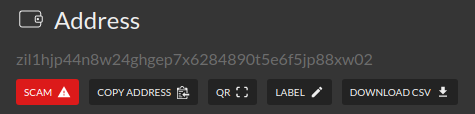
Some scammers may create a Zilliqa address and use phishing techniques to trick people into transferring $ZIL or other tokens to the address held by the scammer. On identification of such scam addresses, the Scam Tracker admin can proceed to mint 1 $SCAM token to the scammer’s address. $SCAM is a ZRC-2 token. It cannot be burnt or transferred by the scammer. Only the Scam Tracker admins can burn $SCAM token.
Issuing $SCAM is like tagging and labeling an address as being potentially used by the scammer. Wallets and explorers can then retrieve the list of $SCAM token holders and proceed to warn their users if the user attempts to lookup or send the token to the scam address.
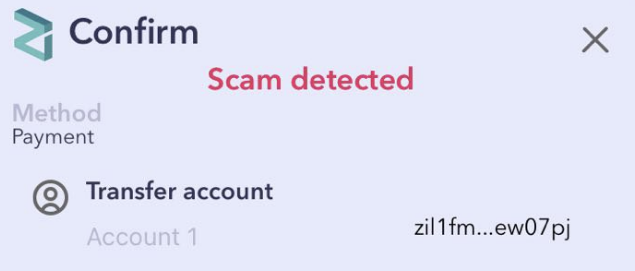
Authentication of Telegram admins
Another common source of scams comes from Telegram DMs and groups. Scammers tend to impersonate an existing admin of the official Zilliqa Telegram groups and lure users into a phishing site or sending cryptocurrency to their own wallet address.
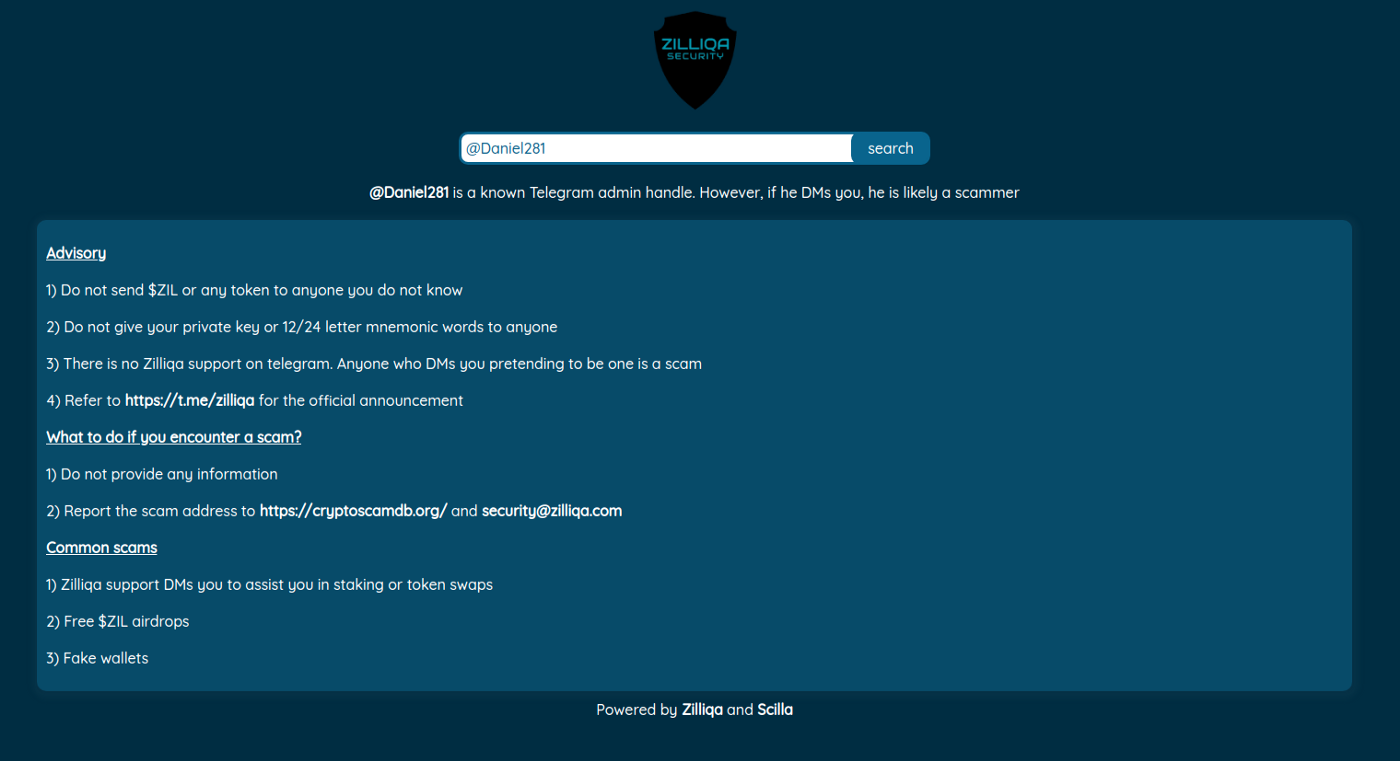
“ManagerTracking.scilla” stores a list of Telegram admins on the official telegram chat groups. Users can visit https://security.zilliqa.com/ and paste in a Telegram ID to check whether a Telegram user is indeed an admin or not. Additionally, it will also display some security advisories.
For further information, please visit or join: